
![]() The “Stop Sexual Abuse” series is designed to provide ministry leaders with information to better understand the risk of child sexual abuse and take necessary steps to protect children in ministry programs.
The “Stop Sexual Abuse” series is designed to provide ministry leaders with information to better understand the risk of child sexual abuse and take necessary steps to protect children in ministry programs.
The first article in the series provided analysis concerning sexual abuse risk using the metaphor of building the right fence. In this article — the second in the series — we will further develop that metaphor.
By Gregory Love & Kimberlee Norris
A SYSTEM BASED ON GROOMING
When a ministry gathers children or youth, it becomes an attractive target for the sexual offender. Preferential offenders — abusers who prefer a child as a sexual partner — generally target a child within an age range and gender of preference.
In developing an effective safety system, churches or ministries are building a “fence”: a protective device meant to keep out an unwanted intruder. Building the right type of fence requires us to understand how an offender will pursue and harm children. Understanding the grooming process of the preferential offender is the key. When we understand the behavior of the offender, we can design and construct effective barriers.
At the core of an effective safety system is this reality: what we believe shapes what we DO. Sexual Abuse Awareness Training changes what we believe. Prevention starts with awareness.”
Critical Concepts
Because the preferential offender often looks like you and me, we cannot recognize him or her visually; we must recognize the risk behaviorally — that is, we must recognize the grooming process.
The grooming process of the preferential offender involves two significant efforts: grooming the child and grooming the gatekeepers.
The targeted child is groomed for inappropriate sexual interaction, while gatekeepers (parents, ministry leaders, co-workers) are groomed into a belief that the offender is a helpful, responsible and trustworthy individual. The effort aimed at gatekeepers is necessary, as all abusers are working to facilitate trusted time alone with a targeted child.
The Grooming Process
Validated by decades of academic studies, the grooming process of the abuser is known and recognizable. The grooming process includes the following steps, with some variation depending on the age of child, gender of child and particular program:
- Gaining access to children within an age and gender of preference;
- Selecting a specific child (or children);
- Introducing nudity and sexual touch; and
- Keeping the child quiet and the abuse secret.
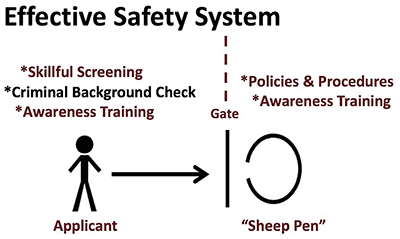
AN EFFECTIVE SAFETY SYSTEM
The purpose of this article is not to simply list elements of an appropriate safety system; rather, it aims to provide analysis of the risk and how the risk relates to specific safety system elements. An understanding of the risk drives preventative efforts.
The Elements of a Safety System
An Effective Safety System must employ the following elements:
- Sexual Abuse Awareness Training
- Skillful Screening (and training)
- Appropriate Criminal Background Check
- Tailored Policies & Procedures
- Systems for Monitoring and Oversight
Each of these elements play a role in a system; no one element solves the problem.
The preferential offender is a “wolf” who will deceive and manipulate to gain access to the “sheep pen” with the intention of doing great harm. In every church, there should be a gate through which anyone desiring access to children must pass, as well as controls in place to identify those with wolf-like qualities.
Within the sheep pen, there must be preventative protocols in place to ensure that grooming behaviors are clearly identified, addressed in policies, recognized by workers and reported to ministry leaders.
To better understand the elements of an effective safety system, the following diagram is helpful:
Sexual Abuse Awareness Training
 Sexual Abuse Awareness Training is the foundation of the safety system, because we cannot address a risk we do not understand. At the core of an effective safety system is this reality: what we believe shapes what we DO. Sexual Abuse Awareness Training changes what we believe. Prevention starts with awareness.
Sexual Abuse Awareness Training is the foundation of the safety system, because we cannot address a risk we do not understand. At the core of an effective safety system is this reality: what we believe shapes what we DO. Sexual Abuse Awareness Training changes what we believe. Prevention starts with awareness.
Awareness Training equips staff members and volunteers with a better understanding of abuser characteristics, the abuser’s grooming process and common grooming behaviors. Awareness Training equips ministry workers with ‘eyes to see’ such that they might recognize abuser characteristics and behaviors.
Critical training topics include:
- Facts and misconceptions
- Common abuser characteristics
- The abuser’s grooming process
- Common grooming behaviors
- Peer-to-peer abuse
- Short- and long-term impacts of abuse
- Reporting requirements
Further, what we believe shapes what we SAY. When staff members and volunteers are trained to understand grooming behaviors, all are better equipped to receive and report allegations and suspicions of abuse, both internally and to appropriate civil authorities.
“Sexual abusers go to where the barriers are lowest or do not exist. Too often, the Church is where the barriers are lowest.
Skillful Screening
The best predictor of future behavior is past behavior. Screening is the process by which ministry leaders gather information about an applicant’s past behavior to best develop expectations regarding future behavior. An effective screening process typically includes: application, reference checks, criminal background check and an interview.

Commonly, ministries screen applicants for fitness for purpose — gathering information about an applicant’s past behavior to determine whether he or she has the skills, abilities and education to fill a particular role. For example, if a school desires to hire a Greek teacher, it is important to gather information to determine whether the applicant has mastered Greek and can effectively teach it. In this example, the school’s purpose for screening was related to fitness for purpose (teaching Greek), not child safety.
Screening for child safety requires the gathering of information concerning an applicant’s past behavior to determine if the applicant has ‘wolf-like qualities.’ Where child safety is concerned, an effective screening process includes questions designed to elicit high-risk indicators of the preferential offender (male and female).
Every applicant — paid or unpaid — should be screened before that applicant may gain access to children. The goal: keep the wolf out of the sheep pen.
Tragically, many ministries are not screening effectively. In fact, many churches are not screening at all.
Because the screening element of an effective safety system is complex, it will be handled in greater detail in our next article.
Criminal Background Check
Most ministries require criminal background checks; however, these often are the sole effort to screen for child safety. This is because ministry leaders lack any real understanding of the realities of the criminal justice system and the known limitations of criminal background checks.
Consider this statistic: Less than 10% of sexual abusers will encounter the criminal justice system, ever.
Given this reality, even if a ministry’s background check system is working perfectly (which is unlikely), more than 90% of individuals who have sexually abused children have no past criminal record … and they know it. So, while making a reasonable effort to access past criminal history has become a standard of care, background checks cannot serve as a standalone safety effort.
Background checks can be a helpful tool when used effectively, however. For each staff member or volunteer, the depth of criminal background check should be determined by the extent of direct contact with children. In addition, background checks should be periodically refreshed.
To become informed consumers, ministry leaders have much to learn about criminal background checks. A subsequent article will discuss criminal background checks in greater detail, providing information about often overlooked high-risk indicators: plea-down offenses, stair-step offenses, grooming offenses, and more.
Tailored Policies & Procedures
A Policies and Procedures document is the written expression of what is and is not permissible behavior in the sheep pen. Effective policies are shaped around an understanding of the abuser’s grooming process, abuser characteristics and common grooming behaviors.
Ministry policies should be tailored to the particular program and population served.
While common grooming behaviors exist universally, the grooming process will vary depending on the age and gender of child, and the type of program. Because grooming will unfold differently in a Student Ministry than in a Mom’s Day Out, policy provisions will vary.
Through Awareness Training, staff members and volunteers can be trained to better understand the purpose of policies, therefore serving more effectively within policy boundaries, and recognizing problematic behaviors before inappropriate sexual interaction occurs. As well, when policy ‘bright lines’ are clearly communicated — communicating, ‘This is appropriate; this is NOT’ — staff members and volunteers are more likely to notice and communicate when someone steps over the bright line. Written policies should present clear guidelines concerning appropriate touch, talk, boundaries, social media interaction, bathroom use, one-to-one interaction, overnight stays and reporting requirements.
SEXUAL ABUSE AWARENESS TRAINING
Sexual Abuse Awareness Training is the foundation of any effort to reduce the risk of child sexual abuse. At the core of this training is a description of the molester’s grooming process: the process used by an abuser to gain access to a child, prepare the child for inappropriate sexual interaction, and then keep the child silent.
This training provides these elements of instruction:
- Facts versus Misconceptions
- Abuser Characteristics
- Grooming Process
- Common Grooming Behaviors
- Peer-to-Peer Sexual Abuse
- Impact of Abuse
- Reporting Requirements
Recognizing the abuser’s grooming process is the focus — allowing child-serving workers to see risky behavior before an abuser has harmed a child.
Training Staff Members and Volunteers
We can’t address a risk we don’t understand. Sexual offenders have no visual profile; they look like everyone else. Instead, abusers are characterized by their behavior.
Sexual Abuse Awareness Training equips staff members and volunteers with a better understanding of abuser characteristics, the abuser’s grooming process and common grooming behaviors.
Critical for Policy Implementation
Nobody likes change if the need for change isn’t understood.
Without effective training, staff members and volunteers rarely embrace change, even in the form of well-crafted policies. Policies work best when ministry workers are trained to understand the WHY, particularly if a policy is new.
Opt-out Opportunity
Sexual Abuse Awareness Training should be completed during the onboarding of any child-serving applicant. When a ministry requires training before the applicant has access to children, an applicant with wrong motives recognizes that all his or her future co-workers understand the grooming process, common grooming behaviors and the importance of reporting. All workers — paid or unpaid — are equipped to recognize the abuser’s attempts to groom children for abuse, with eyes that see, ears that hear and mouths that speak.
Sexual Abuse Awareness Training provides offenders with an opportunity to self-select OUT.
MinistrySafe Training
Sexual Abuse Awareness Training is the cornerstone element of the wide-ranging resources available at MinistrySafe.com. At present, MinistrySafe’s online Awareness Training is being used by more than 25,000 churches, 20 denominations, 400 schools and 10 seminaries — and growing daily.
In 2019, MinistrySafe issued its one-millionth certificate of completion and continues to train more than 35,000 people per month online.
Systems for Monitoring and Oversight
Child sexual abuse is an enormous issue causing incredible harm to children.
For any safety system to remain effective, every ministry must incorporate systems for monitoring and oversight to ensure that you DO what you SAY you do in an ongoing manner.
To this end, a periodic review of safety system elements is necessary:
- Does the system still fit the ministry?
- Are adequate methods of accountability in place?
- Is the ministry able to archive evidence of safety system compliance?
Leaders must evaluate new programs for child protection issues, monitor changes in reporting requirements, address ongoing need for policy updates, and include child protection compliance in employee performance evaluations. Periodic review ensures that child protection is not jeopardized by the departure of one or two key staff members or volunteers.
A system for monitoring and oversight provides the framework for the existence of an effective safety system and ensures the
system’s sustainability.
At MinistrySafe, a safety system is made sustainable through the use of an online Control Panel. To learn more, visit MinistrySafe.com.
Sexual abusers go to where the barriers are lowest or do not exist. Too often, the Church is where the barriers are lowest.
Designing an effective system starts with ministry leaders understanding the behavior of the sexual abuser so that an effective safety system — one with appropriate efforts guarding the sheep pen, and also within it — can be put in place.
Kimberlee Norris and Gregory Love are partners in the Fort Worth, Texas law firm of Love & Norris and founders of MinistrySafe, providing child sexual abuse expertise to ministries worldwide.
After representing victims of child sexual abuse for more than two decades, Love and Norris saw recurring, predictable patterns in predatory behavior. MinistrySafe grew out of their desire to place proactive tools into the hands of ministry professionals. Love and Norris teach the only graduate-level course on Preventing Sexual Abuse in Ministry as Visiting Faculty at Dallas Theological Seminary.


